Part III – SASL Integraton with OpenLDAP
In Part III, OpenLDAP pass thru authentication with a Kerberos Backend using SASL will be demonstrated. Continue reading “Heimdal Kerberos, SASL, and OpenLDAP Integration on FreeBSD – Part III”
Ruminations and Random Contrived Thoughts ….
In Part III, OpenLDAP pass thru authentication with a Kerberos Backend using SASL will be demonstrated. Continue reading “Heimdal Kerberos, SASL, and OpenLDAP Integration on FreeBSD – Part III”
In Part II, a Master/Slave Kerberos implemenation will be configured together with the necessary tools to replicate/propagate the Heimdal Database from Master to Slave Kerberos Servers. Continue reading “Heimdal Kerberos, SASL, and OpenLDAP Integration on FreeBSD – Part II”
In Part I, configuring a Heimdal Kerberos Server and Client is demonstrated. Additionally, SSH will be configured to allow single sign on using Kerberos. Continue reading “Heimdal Kerberos, SASL, and OpenLDAP Integration on FreeBSD – Part I”
After going through this exercise, several aspects of the software configuration needed cleaning up.
Continue reading “OpenLDAP Multi-Master Replication in FreeBSD – Part VIII: Clean Up”
In an effort to provide some level of control to the OpenLDAP Server, access control policy (ACP) can be implemented using the “access to” directive. This article will not focus as an instructive tutorial on access control or ssf (security strength factor) within OpenLDAP, but rather a brief insight into the author’s immediate needs to provide an initial level of directory security using the access control mechanisms. Continue reading “Openldap and Multi-Master Replication in FreeBSD – Part VII: Access Control Policy and SSF”
What’s the use of having an OpenLDAP Directory if you do not have any clients connected to it? In this article, attaching a Macintosh 10.9 Client to the OpenLdap Directory with standard schemas and storing the contents of our Home Directory on a NFS File Server is demonstrated.
 Continue reading “Openldap and Multi-Master Replication in FreeBSD – Part VI: Connecting Clients”
Continue reading “Openldap and Multi-Master Replication in FreeBSD – Part VI: Connecting Clients”
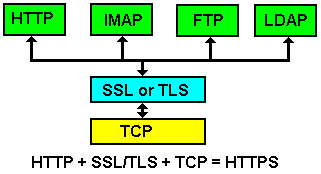
With the advent of NSA snooping, corporate espionage, and general employee mischief, it’s time to start utilizing encryption to snoop-proof data streams emanating from corporate networks. LDAP is but one of many protocols in which encryption is necessary – see flowchart below. This article will focus on using TLS/SSL on the interconnected streams of data originating from and to an OpenLDAP Server and its dependent services. It will not contain much in the area of OpenLDAP ACL’s as a means to segregate different users and data with differing levels of encryption, nor will it focus on SASL and Kerberos as a means to secure data. Again, these topics will present themselves in a future related article.
In Part IV, nss-pam-ldapd and /etc/nsswitch.conf are configured to allow the OpenLDAP server to provide user account, group, host name, etc. that would normally come from /etc/passwd, /etc/group, or NIS. Continue reading “Openldap and Multi-Master Replication in FreeBSD – Part IV: Name Server Switch Setup”
In Part II of this series, phpLDAPadmin was installed and configured to manage an OpenLDAP Directory. Part III will demonstration OpenLDAP Replication using Syncrepl N-Way Multi-Master configuration. Continue reading “Openldap and Multi-Master Replication in FreeBSD – Part III: Replication”
In the last article, we demonstrated setting up and configuring a basic OpenLDAP Server for authentication. However, to manage your newly minted OpenLDAP Directory, a front-end to provide that functionality. In this post, Apache 2.4, PHP 5 and phpLDAPadmin will be installed and configured to manage your Directory. Continue reading “Openldap and Multi-Master Replication in FreeBSD – Part II: PHPLdapAdmin”